After yet another workout where my sports watch completely lost GPS, I’d had enough. I decided to dig into its firmware and pinpoint the problem. I couldn’t find it published anywhere. No download section, no public archive, nothing. So, I changed tactics and went in through the Android app instead, hoping I could pull the firmware out from there. That’s where this story really begins.
[Read More]Evolution of vulnerabilities in Android apps
The history of Android app development has gone through several notable stages, from small apps running locally, to client-server apps, app ecosystems, and super-apps. Each of these stages raised the bar of complexity, creating new vulnerabilities, and increased developers’ concern about the security of both the applications and the data they operate with. The operating system itself has evolved, providing developers with more options and security mechanisms. But there are always a few more unknowns in this system of equations than meets the eye. This article will cover how mobile app vulnerabilities have evolved, what influenced them, what vulnerabilities are relevant now, and what’s in store for the future.
[Read More]Mobile application security
In 2022, our team discovered 216 vulnerabilities during studies of 25 pairs of apps for Android and iOS platforms. The storage of user data in clear text accounted for the largest share of vulnerabilities (14%). Despite the efforts of operation system developers and secure application development communities, this class of vulnerability has continued to be the most prevalent for several years in a row. This trend will remain relevant in 2023, although it is now very simple to use cryptography in mobile applications: both vendor and open-source solutions make working with cryptographic primitives easier for developers. Vulnerabilities related to application integrity checks and storing confidential information in the code shared second place, with 9% each. Third place (8%) was taken by vulnerabilities related to untrusted environment checks.
[Read More]Creating mTLS reverse proxy with Ktor
If you like to integrate with external security systems, then you have probably come across such a thing as Mutual TLS (also known as TLS mutual authentication or mTLS). There is nothing particularly difficult in such integration. Except for two nuances:
- Integration will have to be done in each service
- In each service you need to put client certificates for passing the mTLS handshake
And if you can somehow live and put up with the first nuance, then the second already causes much more problems and leads to sad faces of your security team. To make them happy again, and at the same time eliminate the need to write the same code in each service, can be made by a smart reverse proxy, which will take all the hardships and hardships handshake related and possibly some other additional logic. We will do this farm on Ktor, because why not;)
To make them happy again, and at the same time get rid of the need to write the same code in each service, we will write a smart reverse proxy which will take care of all hardships associated with an mTLS handshake and other security logic. I will implement all these things with Ktor, because why not ;)
[Read More]Installing Drozer on macOS Catalina
In general, I don’t use Drozer. And using this tool on macOS is unusual for me. If I do some “pentest things” I just take my Kali Linux with pre-installed Drozer and use it there. But the day has come, and I decided to install Drozer on my macOS. It was a real hell =)
I spent a lot of time trying to make it work. Eventually, I had to rewrite a piece of class loader script… A living hell! When everything started working right, I came up with a better way of installing Drozer on macOS and removed all this stuff . In fact, there are two good ways to do it. The Docker-way and the following one
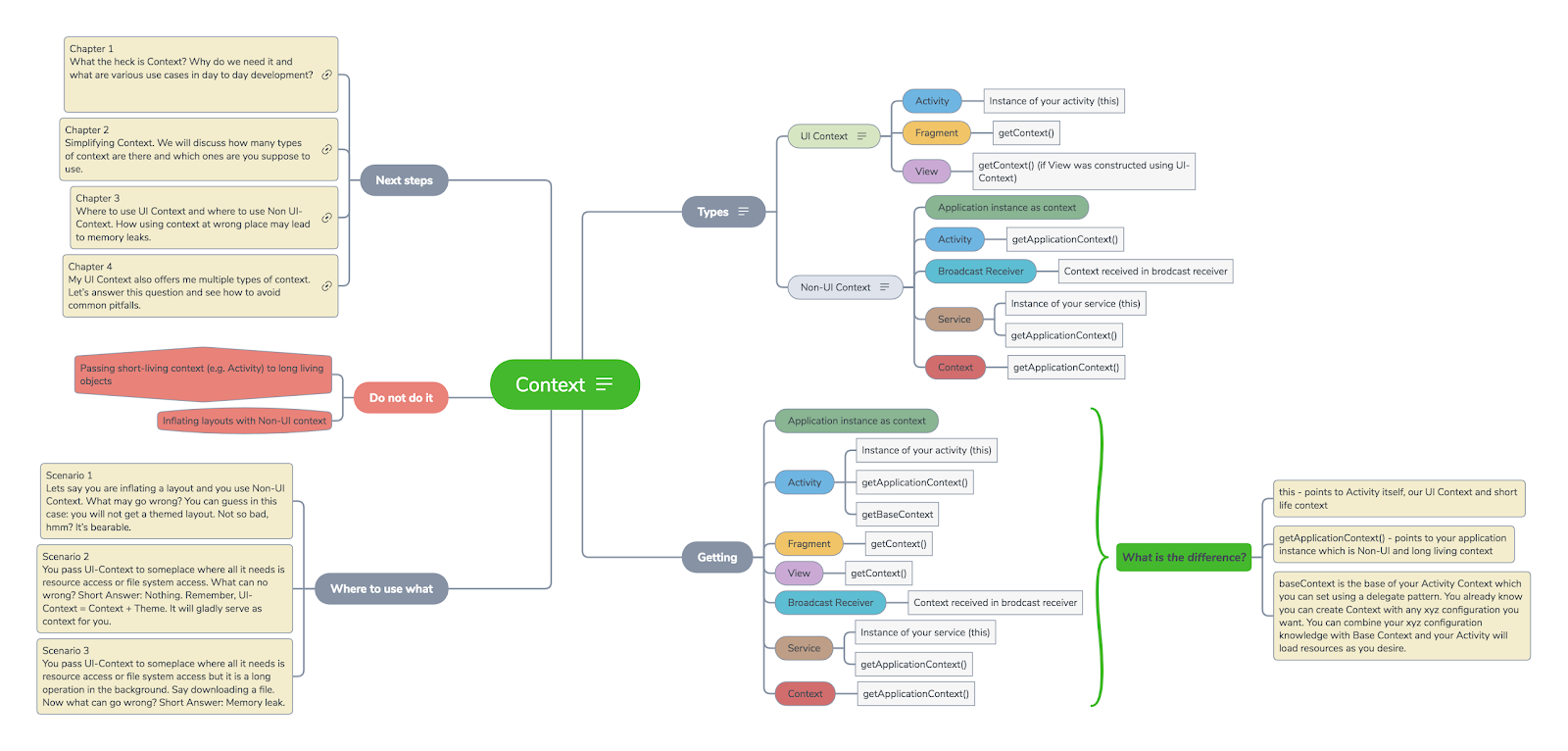
[Read More]Android Context
I’ve come across an interesting article and want to share you my notes based on it. I made these notes as the mind map.
Original article: Mastering Android context
XMind file: Download
Elemental Design Patterns (book). My review and notes.
Recently, I read this book and want to share my thoughts about it with you.
If you already know about GoF and their Design Patterns then the book will be a godsend for you. The author (and his team) did a great job to spread out GoF’s patterns into tiny, elemental patterns and to present the result to us. Why is it significant? It helps to understand the “big patterns” better and even build your own patterns.
To tell the truth, the first half of the book seemed to me very boring. A lot of reasoning about “the meaning of life” and etc. I even wanted to stop reading it. Then I understood what this book is really about and read it from cover to cover.
[Read More]